The following issue occurred for one of my customers after enabling MFA for all users. The directory synchronization stopped working.
The above situation may not occur often as usually you are excluding trusted locations (aka your corporate network public endpoints) from applying conditional policies – especially when enabling MFA – and your Azure AD Connect instance is running on a server hosted on-premises.
That said, you may also have extended your on-premises AD to Azure (running domain controllers on Azure VM) and probably also have setup a standby Azure AD Connect instance on an Azure VM too for fault tolerance.
What happened?
After trialling Azure MFA with pilot users, MFA has then been turned on for all users using conditional access configured to not request MFA when connected from the corporate network.
The customer environment is running on Azure Virtual Machines, with Azure AD Connect instance running on one of these VM’s.
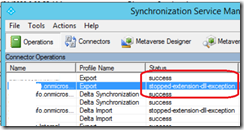
After turning on MFA for all users, the directory synchronization stopped working with the following errors/information:
- in the Azure AD Connect console, the import and export from/to Azure AD steps stopped with the error “stopped-extension-DLL-exception” with no further details; off course the password synchronization also stopped working
- In the Application event log, the following error was logged
Log Name: Application
Source: ADSync
Date: 1/21/2020 9:00:55 AM
Event ID: 6900
Task Category: Server
Level: Error
Keywords: Classic
User: N/A
Computer: <removed>
Description:
The server encountered an unexpected error while processing a password change notification:
“The ADSync service is not allowed to interact with the desktop to authenticate Sync_<removed>@<removed>.onmicrosoft.com. This error may occur if multifactor or other interactive authentication policies are accidentally enabled for the synchronization account.at TargetExtensionManager.Ping(TargetExtensionManager* , ECMAInformation* ecmaInformation, Char* state, Int32* result)
InnerException=>
none
“
Solution
So we went back to the Conditional Access policy requesting for MFA and set it to exclude the Directory Synchronization Accounts role and the directory synchronization starts working again immediately.
Conclusion
It can be a good thing to always exclude the Directory Synchronization Accounts from getting conditional policies being applied to them.
This will cause any threats as these accounts are generated only by Azure AD Connect during the initial setup and they have specific settings/permissions.

![image_thumb[1] image_thumb[1]](https://www.cubesys.com.au/wp-content/uploads/2020/01/image_thumb1_thumb-84.png)
![image_thumb[2] image_thumb[2]](https://www.cubesys.com.au/wp-content/uploads/2020/01/image_thumb2_thumb-64.png)
