As you know, Microsoft Edge has now replaced the Intune Managed Browser for mobile devices managed with Intune/Endpoint Configuration Manager.
Well, with Intune/Endpoint Configuration Manager you can now also define an application configuration policy to define the websites end-users can or can not access using the Edge managed browser.
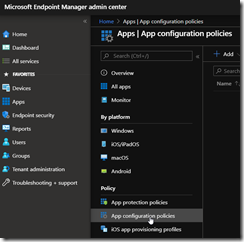
To manage which website is allowed for access, logon to your Intune/Endpoint Configuration Manager portal (https://endpoint.microsoft.com/) and access the AppsApp configuration policies blade to create (or edit) the Application Configuration policy for Microsoft Edge
NOTE you can only define either the allowed or blocked URL’s settings, not both at the same time; if you want to manage both you will need to create 2 policies
Depending of the application policy type – Managed devices or Managed apps – the configuration options are a little bit different; the easiest one is the Managed Apps
With the Managed Apps you can target at once both Android and iOS devices while the Managed Devices requires you create 2 different rules for each mobile OS.
When using the Managed Apps policy type, the option to define which website is allowed or not is available in the Settings blade
The setting Redirect restricted sites to personal context, which is set to true by default, ensures that if the user has added his or her personal account into the app, then Edge can open the restricted site in the user’s personal account context or possibly in the Azure AD account’s InPrivate context.
If you use the Managed devices policy type, the options to manage allowed/blocked URL’s are available in the Settings blade by adding the following configuration keys:
- Block access to a list of URLs
- Allow access to a list of URLs
When configuring the list of URLs don’t forget to manage both HTTP and HTTPS.
When using the Managed devices, the list of URLs must be in the following format – note the | to define a list of URLs: http://url1|https://url1
You can use a wildcard to define multiple URLs at once; for example https://*.microsoft.com will block all subdomain of the microsoft domain.
When the policy is applied, end-users will get notified when they try to access unauthorized website; depending if you allow the redirection to the personal context, the message will be a little bit different:
You can get the complete list of available settings for Edge here http://aka.ms/edgeappconfig

![image_thumb[1] image_thumb[1]](https://www.cubesys.com.au/wp-content/uploads/2020/05/image_thumb1_thumb-152.png)
![image_thumb[2] image_thumb[2]](https://www.cubesys.com.au/wp-content/uploads/2020/05/image_thumb2_thumb-121.png)
![image_thumb[3] image_thumb[3]](https://www.cubesys.com.au/wp-content/uploads/2020/05/image_thumb3_thumb-98.png)
![image_thumb[4] image_thumb[4]](https://www.cubesys.com.au/wp-content/uploads/2020/05/image_thumb4_thumb-78.png)
![image_thumb[6] image_thumb[6]](https://www.cubesys.com.au/wp-content/uploads/2020/05/image_thumb6_thumb-41.png)
![image_thumb[5] image_thumb[5]](https://www.cubesys.com.au/wp-content/uploads/2020/05/image_thumb5_thumb-53.png)
